

To satisfy the needs identified in the requirement analysis, a multi-tiered approach to the design is preferred. In particular, the components that effect the necessary changes to the system configuration based on actions taken within the UMS should be isolated from the rest of the system. In this way, a migration to a new server or a new operating system release will require changes to these components without incurring the complete system rewrite that the current migration entails.
At the same time, where multiple procedures require the same function, a list of shared libraries should encapsulate these functions for this same reason. In this way, functions and services specific to the current version of RedHat (such as user authentication) can easily be altered to take into account new features or services of future releases.
However, to leverage volunteer resources, the tasks of developing the web interface (a task best suited to web developers) are separated from the tasks of developing back-end functionality (a task for formal PERL programmers). This distinction has the added benefit of allowing the web interface to be updated to a new corporate look in the future without affecting the application logic.
As depicted in Figure 1 below, the develop effort can be broken into a number of conceptual parts:
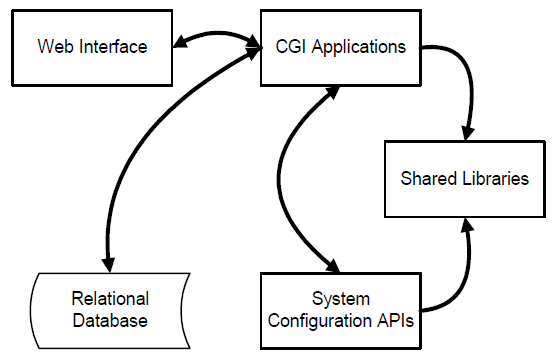
Before development of the Web Interface, a Visual Identity Guide (VIG) will be required. This guide will contain the basic style elements to ensure that all pages on the User Interface are visually and thematically consistent with each other and with the general GPFN web site.
The Visual Identity Guide will also contain directives concerning how users will navigate around the pages as well as how linkages outside the UMS pages back to the GPFN general web site will be incorporated.
In addition to the VIG, web developers will require a common set of resources such as icons, navigation bar graphics, template files and HTML Style. Developing the VIG and the other components will be the duty of the GPFN webmaster.
All System Configuration APIs must be intrinsically distrustful of their calling functions. This prevents a potential malefactor from directly calling these programs while masquerading as coming from a valid user. Such a masquerade could be successful if the API did not verify the authenticity of the caller on its own.
This distrust is managed by creating a virtual domain within the webserver for the UMS. The virtual domain along with its libraries and system configuration APIs will run under a distinct set of user and group permissions.
The Password Change API is responsible to ensure that the username and old password successfully authenticate the user. Only if the user is verified in this way is the new password checked for hardness according to the system configuration (normally using the cracklib libraries), then using a suid program, this API effects the password change on the system.
The Mail Forwarding API authenticates the user and if authenticated, allows the user to review, change or set the contents of their home .forward file.
The Mail Filtering API can perform many functions. For the purpose of this application, it copies a system .procmailrc template file into the user’s home account, thus effecting spam control. Again, the API must authenticate the user before effecting these changes.
The Disk Quota API authenticates the user and once authenticated, returns the user’s current quota values for display back to the user via a CGI script.
The Shared Library functions include all functions and methods used by two or more components of the system. It will include user authentication and managing of session credentials.
These functions will involve setting and retrieving cookies on the user’s browser, writing to and retrieving session values from the relational database, and managing Object Oriented PERL constructs and entities.
User authentication involves comparing the username supplied on a web form with the existence of the username on the system then comparing the password supplied on the form with the password maintained for the account on the system.
On a modern Linux system, Pluggable Authentication Modules, or PAM, supports user PAM supported libraries and applications are available on the Internet to be used as a template in constructing a custom authentication package.
For the UMS, a web form will request a user to input his username and password. PAM will then authenticate this user. If the user is successfully authenticated, a session token will be created for the user. This token will have an expiry date one hour into the future.
Authenticating GPFN volunteers is a slightly different matter. A GPFN volunteer is not simply a user, but rather a user with increased permissions to the system this system may not be suitable for volunteers. As well, volunteers may not want to use their system password to authenticate themselves to the UMS. Instead, they may want to use a password specific to the UMS.
For this reason, authenticating GPFN volunteers will use the htaccess and htpasswd functions inherent in the Apache web server. Web pages and CGI scripts specific to volunteers will be in a separate directory under which the web server will apply access controls.
Once the system authenticates a user, the libraries will have to manage session persistence for the user. To effect this persistence, the libraries will have their own database in the RDBMS. When a user is authenticated, a session token will be created composed of the username, the access level, the session creation timestamp, and a unique pseudo-random session ID. This token is inserted into the database and a cookie with this session token will be sent back to the user’s browser.
From then on, any calls by the user to a page on the system will return the cookie. This cookie is matched with the cookie in the database. If a match exists, then the user is the holder of a currently valid session. Any of the following conditions indicates that the session is not currently valid:
In any of these cases, the user is redirected back to the login page with the current pages’ URL stored in the QUERY_STRING for re-authentication and the session token is deleted from the database and the cookie. Once re-authenticated, the stored URL can be used to return the user to the page they were viewing before the authentication failure.
The system implementation involves a number of distinct yet inter-related functions. The following dataflow diagrams show the interaction flows in the system. The last dataflow case: “Manage User Account” is slated for Phases 2 and 3 of the project.
The top-level dataflow diagram lists the interactions between the system. This interaction is further exploded for each dataflow in the subsequent diagrams:
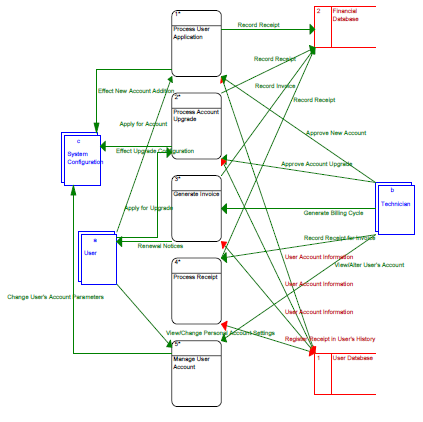
The Manage User Account Data Flow is slated for implementation in phases 2 and 3 of the project.
The dataflow will be managed using a combination of HTML pages, Javascript functions within HTML, CGI scripts, embedded PERL within HTML, and some shell script and PERL script library functions.
To visualize the data flow as it relates to the actual structure of the web site, the following Web Navigation Flow Diagrams were prepared. Figure 2 shows the pages available through the public web space to all users and potential users. Note that while an initial applicant can make an application without any sort of authentication, a user requesting an upgrade and all other user functions require the user to be authenticated prior to performing any of these actions.
The volunteer portion of the web site will be secured using the inherent access controls of the Apache web server. As such, no user authentication library calls are required, the processing flow is somewhat simplified.
The Data Model is intended to be a comprehensive model to support both the immediate needs of the UMS and possible future features and enhancements. Not all fields will be used in the currently scoped implementation.
| Data Type | Constraints | Default Value | Description | |
|---|---|---|---|---|
|
Sys_Default_Id |
Int |
Primary Key |
|
System Generated Sequential Key |
|
Sys_Ind_Mem_Price |
Float |
Not NULL |
24.00 |
Approved Annual Fee for Individual Memberships |
|
Sys_Inst_Mem_Price |
Float |
Not NULL |
48.00 |
Approved Annual Fee for Institutional Memberships |
|
Sys_Reg_User_Price |
Float |
Not NULL |
0.00 |
Approved Annual Fee for Registered Non-member users |
|
Sys_PPP_Price |
Float |
Not NULL |
125.00 |
Approved Annual Fee for Graphical PPP Access |
|
Sys_DB_Price |
Float |
Not NULL |
|
Approved Annual Fee for Database Hosting |
|
Sys_VirtualDomain_Price |
Float |
Not NULL |
|
Approved Annual Fee for Virtual Domain Hosting |
|
Sys_TimeQuota1 |
Float |
Not NULL |
? |
Maximum allowed time per single session for users |
|
Sys_TimeQuota2 |
Float |
Not NULL |
? |
Maximum allowed sessions per day for users |
|
Sys_SSL_Price |
Float |
Not NULL |
|
Approved Additional Annual Fee for SSL encrypted Virtual Domain Hosting |
|
Sys_ListServer_Price |
Float |
Not NULL |
100.00 |
Approved Annual Fee for Listserver Hosting |
|
Sys_Next_UserId |
String (5) |
Not NULL |
|
Next available UserName for Registered User accounts following the Csuite naming convention of aannn1 |
|
Sys_ExtraDiskQuota_Price |
Float |
Not NULL |
? |
Approved Annual Pricing per Mb of extra Disk Quota above the approved included amounts |
|
Sys_Incl_Quota1 |
Int |
Not NULL |
|
Approved Amount of basic disk space in filesystem1 |
|
Sys_Incl_Quota2 |
Int |
Not NULL |
|
Approved Amount of basic disk space in filesystem2 |
|
Sys_Incl_Quota3 |
Int |
Not NULL |
|
Approved Amount of basic disk space in filesystem3 |
|
Sys_Quota1_Mnt |
String (8) |
Not NULL |
|
Mount point on the system for quota1 |
|
Sys_Quota2_Mnt |
String (8) |
Not NULL |
|
Mount point on the system for quota2 |
|
Sys_Quota3_Mnt |
String (8) |
Not NULL |
|
Mount point on the system for quota3 |
|
Sys_Last_Annual_Cycle |
Timestamp |
|
|
The timestamp of the last generated invoice cycle. This is used to frequent duplicate invoice cycles within the same fiscal year. |
| Field Name | Data Type | Constraints | Default Value | Description |
|---|---|---|---|---|
|
User_Number |
Int |
Primary Key |
|
System Generated Sequential Number |
|
User_LastName |
String (30) |
Not NULL |
|
User’s Last Name |
|
User_FirstName |
String (20) |
Not NULL |
|
User’s First Name |
|
User_Initial |
String (60) |
|
|
User’s Initial |
|
User_Salutation |
String (60) |
|
One of “Mr.”, “Mrs.”, “Ms.”, “Dr.”, “Rev.” |
User’s Title of Address |
|
User_Organization |
String (50) |
|
|
Name of User’s Organization if user is a group or collective entity |
|
User_Title |
String (30) |
|
|
Position or title of person within the organization |
|
User_StreetAddress1 |
String (30) |
Not NULL |
|
User’s first line of mailing address |
|
User_StreetAddress2 |
String (30) |
|
|
|
|
User_City |
String (30) |
Not NULL |
|
|
|
User_Province |
String (30) |
Not NULL |
|
|
|
User_Country |
String (30) |
Not NULL |
|
|
|
User_PostalCode |
String (20) |
Not NULL |
|
|
|
User_HomePhone |
String (20) |
|
|
|
|
User_WorkPhone |
String (20) |
|
|
|
|
User_Age |
Int |
|
|
Really only required for users under the age of majority (so we get their parent’s signature on any application) |
|
User_IsActive |
Int |
Not NULL |
0 |
0 for not active, 1 for active, 2 for declined, 3 for expired, 4 for purged |
|
User_Since |
Timestamp |
Not NULL |
|
Date the user applied for an account |
|
User_IsMember |
Int |
Not NULL |
0 |
0 for non-member, 1 for member |
|
User_Status_Msg |
String (60) |
|
|
Any Volunteer entered text string to describe issues concerning a user |
|
User_UserName |
String (16) |
Not NULL |
|
The system generated username for non- members, or the personalized username for members. This is only used during the account application process and NOT changed for users who upgrade to membership later. |
|
User_InitialPassword |
String (16) |
Not NULL |
Must be checked against the cracklib |
The User requested initial password in MD5 hash encryption |
|
User_EnteredBy |
String (16) |
Not NULL |
|
The name of the GPFN Volunteer adding the user to the system |
| Field Name | Data Type | Constraint | Default Value | Description |
|---|---|---|---|---|
|
User_Number |
Int |
Foreign Key |
References User |
If an entry exists in this table with User_Number, then we know that this User is also a member |
|
Affinity_Number |
String (10) |
Foreign Key |
References Affinity |
If an entry exists in this table, then the member has a special pricing relationship with GPFN (to be implemented in Phase 4) |
|
Member_Type |
Int |
Not NULL |
1 or 2 |
1 for Individual Member, 2 for Institutional Member |
|
Member_Since |
Timestamp |
Not NULL |
|
Date on which user applied to become a member |
|
Member_EnteredBy |
String (16) |
Not NULL |
|
The name of the GPFN Volunteer adding the member to the system |
| Field Name | Data Type | Constraints | Default Value | Description |
|---|---|---|---|---|
|
Affinity_Number |
String (10) |
Primary Key |
|
|
|
Affinity_Name |
String (50) |
Not NULL |
|
Name of group or organization entering into an affinity relationship with GPFN |
|
Affinity_Contact_ LastName |
String (30) |
Not NULL |
|
Name of contact person with the group or organization |
|
Affinity_Contact_ FirstName |
String (20) |
Not NULL |
|
|
|
Affinity_StreetAddress1 |
String (30) |
Not NULL |
|
|
|
Affinity_StreetAddress2 |
String (30) |
|
|
|
|
Affinity_City |
String (30) |
Not NULL |
|
|
|
Affinity_Province |
String (30) |
Not NULL |
|
|
|
Affinity_Country |
String (30) |
Not NULL |
|
|
|
Affinity_PostalCode |
String (30) |
Not NULL |
|
|
|
Affinity_Phone |
String (20) |
Not NULL |
|
|
|
Affinity_Ind_Mem_Price |
Float |
Not NULL |
0.00 |
Agreed price of individual memberships under this affinity agreement |
|
Affinity_Ind_Mem_Max_ Count |
Int |
Not NULL |
0 |
Agreed maximum number of individual memberships to be sold under this affinity agreement |
|
Affinity_PPP_Price |
Float |
Not NULL |
0.00 |
Agreed price of PPP connections under this affinity agreement |
|
Affinity_PPP_Max_Count |
Int |
Not NULL |
0 |
Agreed maximum number of PPP connections to be sold under this affinity agreement |
| Affinity_Quota1_Amt | Int | Not NULL | 0 |
Agreed amount of disk space in Quota space 1 |
|
Affinity_Quota2_Amt |
Int |
Not NULL |
0 |
Agreed amount of disk space in Quota space 2 |
|
Affinity_Quota2_Amt |
Int |
Not NULL |
0 |
Agreed amount of disk space in Quota space 2 |
|
Affinity_Quota_Max_ Count |
Int |
Not NULL |
0 |
Agreed maximum number of members who benefit from the increased quota limits under this affinity |
|
Affinity_Annual_ Agreement_Fee |
Float |
Not NULL |
0.00 |
Annual Fee to be invoiced to the Affinity_Name for the terms of the affinity agreement |
|
Affinity_EnteredBy |
String (16) |
Not NULL |
|
The name of the GPFN Volunteer adding or editing the affinity to the system |
| Field Name | Data Type | Constraints | Default Value | Description |
|---|---|---|---|---|
|
User_Number |
Int |
Foreign Key |
References User |
|
|
Service_Text_Access |
Int |
Not NULL |
1 |
1 if user has access to text-only dial-up |
|
Service_PPP_Access |
Int |
Not NULL |
0 |
1 if user has access to PPP graphical dial-up |
|
Service_WebSite |
Int |
Not NULL |
0 |
1 if user has access to web space within GPFN’s public web space (not including the user’s public_html directory) |
|
Service_Website_Path |
String |
|
|
The relative path from the Webserver’s document root to the directory for this members’ web space within the gpfn.ca domain. |
|
Service_DBAccess |
Int |
Not NULL |
0 |
Number of databases the user has access to on the database server |
|
Service_Quota1 |
Int |
Not NULL |
0 |
Number of extra Mb of disk space the user has subscribed to on the filesystem referenced by Quota1 |
|
Service_Quota2 |
Int |
Not NULL |
0 |
Number of extra Mb of disk space the user has subscribed to on the filesystem referenced by Quota2 |
|
Service_Quota3 |
Int |
Not NULL |
0 |
Number of extra Mb of disk space the user has subscribed to on the filesystem referenced by Quota3 |
|
Service_VirtualDomain |
Int |
Not NULL |
0 |
Number of virtual domains the user has on the system |
|
Service_ VirtualDomainName |
String |
|
|
Registered Name of the Virtual Domain |
|
Service_TimeQuota1 |
Int |
NotNULL |
0 |
Amount of extra time the user has paid to be added to the value included in Sys_TimeQuota1 |
|
Service_TimeQuota2 |
Int |
NotNULL |
0 |
Amount of extra time the user has paid to be added to the value included in Sys_TimeQuota2 |
|
Service_EmailAliases_ Max_Count |
Int |
Not NULL |
0 |
The maximum number of e-mail aliases belonging to this user |
|
Service_SSL |
Int |
Not NULL |
0 |
The number of SSL enabled Virtual Domain web hosts for this user on the system |
|
Service_Listserver |
Int |
Not NULL |
0 |
The number of Listservers for this user on the system |
|
Services_EnteredBy |
String (16) |
Not NULL |
|
The name of the GPFN Volunteer adding or editing this service list on the system |
| Field Name | Data Type | Constraints | Default Value | Description |
|---|---|---|---|---|
|
Alias_Id |
Int |
Primary Key |
|
System Generated Incremental Number |
|
User_Number |
Int |
Foreign Key |
References User |
|
|
Alias_GPFNAddress |
String (30) |
Not NULL |
|
The GPFN address to which mail is received |
|
Alias_ExtAddress |
String (50) |
Not NULL |
|
The non-GPFN address to which mail is redirected |
| Field Name | Data Type | Constraints | Default Value | Description |
|---|---|---|---|---|
|
Invoice_Number |
Int |
Primary Key |
|
System Generated Incremental Number |
|
User_Number |
Int |
Foreign Key |
References User |
|
|
Invoice_Date |
Timestamp |
Not NULL |
|
Date on which the invoice was issued |
|
Invoice_Medium |
String (20) |
Not NULL |
|
One of “e-mail”, “paper”, “fax” or some other such descriptor of the method in which the invoice was delivered |
|
Invoice_Amount |
Float |
Not NULL |
|
The total value of the invoice |
|
Invoice_EnteredBy |
String (16) |
Not NULL |
|
The name of the GPFN Volunteer adding this invoice to the system |
| Field Name | Data Type | Constraints | Default Value | Description |
|---|---|---|---|---|
|
Item_Number |
Int |
Primary Key |
|
System Generated Incremental Number |
|
Invoice_Number |
Int |
Foreign Key |
References Invoice |
|
|
User_Number |
Int |
Foreign Key |
References User |
|
|
Item_Description |
String (60) |
Not NULL |
|
Description of the line item for the invoice |
|
Item_Amount |
Float |
Not NULL |
0.00 |
Amount of the line item for the invoice |
| Field Name | Data Type | Constraints | Default Value | Description |
|---|---|---|---|---|
|
Receipt_Number |
Int |
Primary Key |
|
System Generated Incremental Number |
|
Invoice_Number |
Int |
Foreign Key |
References Invoice |
|
|
User_Number |
Int |
Foreign Key |
References User |
|
|
Receipt_Date |
Timestamp |
Not NULL |
|
Date that the amount was received and processed by the volunteer |
|
Receipt_Amount |
Float |
Not NULL |
0.00 |
Amount received from the user |
|
Receipt_Payment_Type |
String (30) |
Not NULL |
|
One of “Cash”, “Cheque”, “Credit Card” or some other description |
|
Receipt_Entered_By |
String (16) |
Not NULL |
|
The name of the GPFN Volunteer adding this receipt to the system |
| Field Name | Data Type | Constraint | Default Value | Description |
|---|---|---|---|---|
|
Upgrade_Id |
Int |
Primary Key |
|
System Generated Incremental Number |
|
Invoice_Number |
Int |
Foreign Key |
References Invoice |
|
|
User_Number |
Int |
Foreign_Key |
References User |
|
|
Upgrade_User-Ind |
Int |
Not NULL |
0 |
1 if the upgrade turns a registered user into an individual member |
|
Upgrade_User-Inst |
Int |
Not NULL |
0 |
1 if the upgrade turns a registered user into an institutional member |
|
Upgrade_Ind-Inst |
Int |
Not NULL |
0 |
1 if the upgrade turns an individual into an institutional member |
|
Upgrade_Username |
String (16) |
|
|
The selected username for a user upgrading to a membership from a registered user account. |
|
Upgrade_toPPP |
Int |
Not NULL |
0 |
1 if the upgrade enables PPP |
|
Upgrade_toDB |
Int |
Not NULL |
0 |
The number of Databases to be added to the User’s account |
|
Upgrade_DBName |
String |
|
|
The requested name for a database on the database server. |
|
Upgrade_Quota1 |
Int |
Not NULL |
0 |
Number of Mb to be added to the user’s disk quota of the filesystem referenced by Quota1 |
|
Upgrade_Quota2 |
Int |
Not NULL |
0 |
Number of Mb to be added to the user’s disk quota of the filesystem referenced by Quota2 |
|
Upgrade_Quota3 |
Int |
Not NULL |
0 |
Number of Mb to be added to the user’s disk quota of the filesystem referenced by Quota3 |
|
Upgrade_toVirtualDomain |
Int |
Not NULL |
0 |
Number of Virtual Domains to add to the user |
|
Upgrade_ VirtualDomainName |
String |
|
|
The requested domain for an application for a virtual domain |
|
Upgrade_TimeQuota1 |
Int |
Not NULL |
0 |
Number of additional minutes to add to Sys_TimeQuota1 |
|
Upgrade_TimeQuota2 |
Int |
Not NULL |
0 |
Number of additional sessions to be added to Sys_TimeQuota2 for this user |
|
Upgrade_toSSL |
Int |
Not NULL |
0 |
Number of SSL enabled web hosts to be added to this client |
|
Upgrade_toAliases |
Int |
Not NULL |
0 |
Number of additional email aliases to be added to this user’s services |
|
Upgrade_AliasExtAddress |
String |
|
|
e-mail address of the external service to which e-mail to the alias will be redirected |
|
Upgrade_ AliasGPFNAddress |
String |
|
|
e-mail address of the GPFN address to which mail will be receive and then redirected |
|
Upgrade_toListserver |
Int |
Not NULL |
0 |
Number of additional Listservers to be added to this user’s services |
|
Upgrade_ListserverName |
String |
|
|
Name of mailing list for an upgrade to Listserver. |
|
Upgrade_ApprovedBy |
String (16) |
Not NULL |
|
The name of the GPFN Volunteer approving this upgrade on the system |
Links
[1] https://niedermayer.ca/user/login?destination=node/73%23comment-form
[2] https://niedermayer.ca/user/login?destination=node/74%23comment-form
[3] https://niedermayer.ca/user/login?destination=node/76%23comment-form
[4] https://niedermayer.ca/user/login?destination=node/78%23comment-form
[5] https://niedermayer.ca/user/login?destination=node/77%23comment-form
[6] https://niedermayer.ca/user/login?destination=node/79%23comment-form
[7] https://niedermayer.ca/user/login?destination=node/80%23comment-form
[8] https://niedermayer.ca/user/login?destination=node/81%23comment-form
[9] https://niedermayer.ca/user/login?destination=node/82%23comment-form
[10] https://niedermayer.ca/user/login?destination=node/83%23comment-form
[11] https://niedermayer.ca/sites/default/files/large_dfd4.PNG
[12] https://niedermayer.ca/user/login?destination=node/84%23comment-form
[13] https://niedermayer.ca/user/login?destination=node/85%23comment-form
[14] https://niedermayer.ca/user/login?destination=node/86%23comment-form
[15] https://niedermayer.ca/user/login?destination=node/87%23comment-form
[16] https://niedermayer.ca/user/login?destination=node/88%23comment-form
[17] https://niedermayer.ca/user/login?destination=node/89%23comment-form
[18] https://niedermayer.ca/user/login?destination=node/90%23comment-form
[19] https://niedermayer.ca/user/login?destination=node/91%23comment-form
[20] https://niedermayer.ca/user/login?destination=node/92%23comment-form
[21] https://niedermayer.ca/user/login?destination=node/93%23comment-form
[22] https://niedermayer.ca/user/login?destination=node/94%23comment-form
[23] https://niedermayer.ca/user/login?destination=node/95%23comment-form
[24] https://niedermayer.ca/user/login?destination=node/96%23comment-form
[25] https://niedermayer.ca/user/login?destination=node/97%23comment-form